DDCTF 2020 Web WP
本文最后更新于:2022年4月13日 下午
Go实乃知识盲区
这是一篇复现记录,部分思路参考了如下链接,赞美师傅wywwtwx
参考:DDCTF 2020 Writeup - 安全客,安全资讯平台
Web签到题
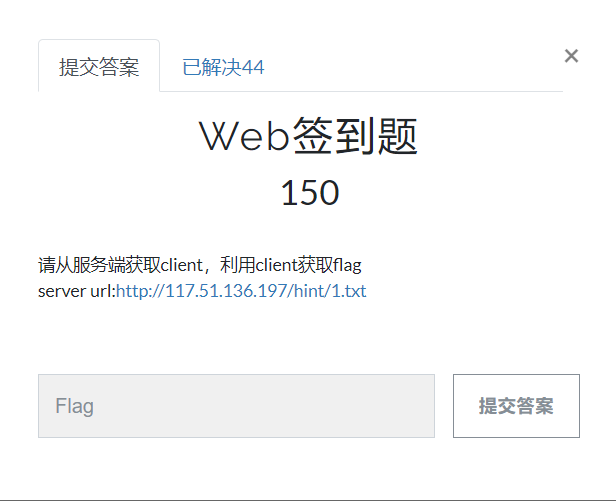
前面的相信大家都懂,是JWT爆破,但还是梳理一下
根据提示在用POST传参可以拿到JWT
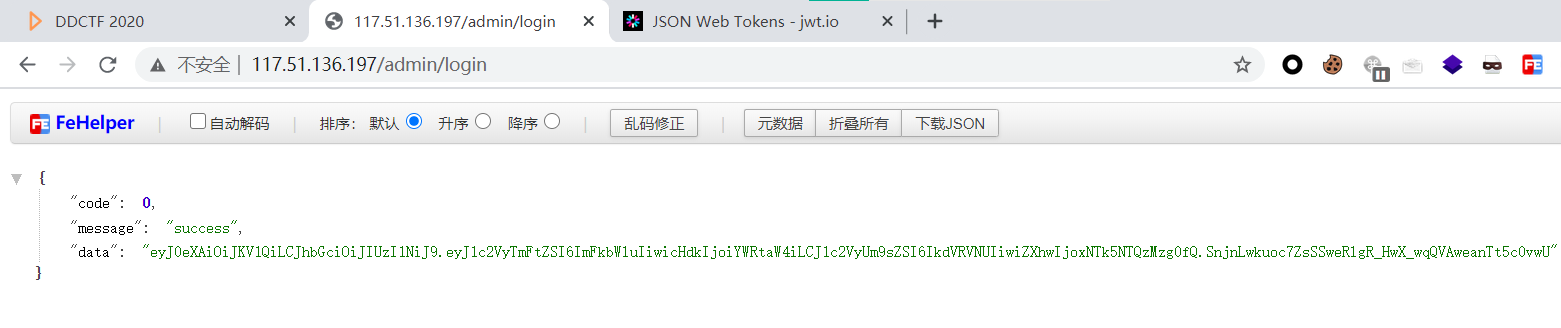
在拿去爆破后可得到Secret值(似乎是你的用户名,然后群里有师傅用户名乱输然后没爆破出来。。)
爆破工具是c-jwt-cracker(需要的自取)
爆破拿到key后去网站https://jwt.io 篡改JWT,而后再次提交
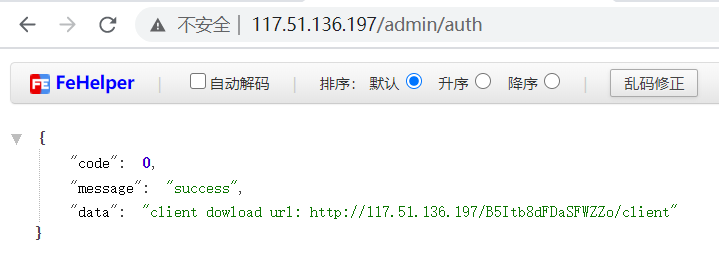
就可以拿到client,自此第一关结束。
第二关是需要在client中构造合法的sign值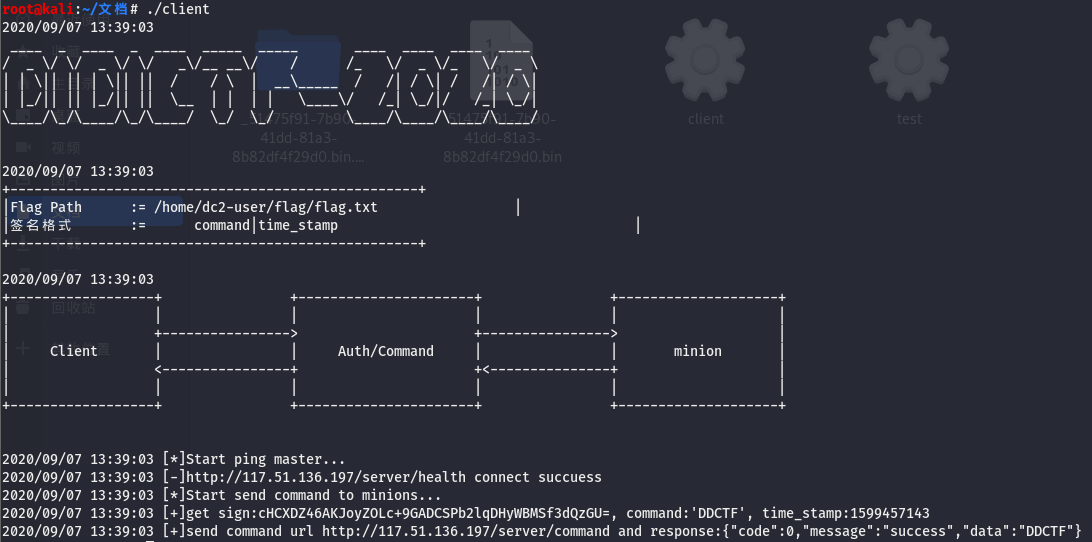
这里可以逆向算法后写脚本,也可以patch,我选的是第一个路子,这块做完后就彻底卡住了
参考:
https://www.anquanke.com/post/id/170332
https://www.anquanke.com/post/id/85694
https://www.jianshu.com/p/7d006f2b4414
关于算法的逆向:
七分逆向三分猜,作为一个Web分类下的题,出题人必然不会在Re上卡我们。刚好我同时算半个Re选手,顺便记录一下当时的心路历程。
当时还不太知道有IDA的Golang插件,不过也是搞了出来。现在顺便加上,看起来也舒服些
https://github.com/sibears/IDAGolangHelper
首先找到我们的关键getSign函数(没有插件可以用老方法String)
1 | |
可以看到有一个很显眼的DDCTFWithYou,还有就是这个
1 | |
crypto_hmac_New这个一出来应该很多人都明白是啥了,先初步猜测这是我们的HmacSHA256(奇怪的是FindCrypt没识别出来),而这个DDCTFWithYou十有八九就是我们的秘钥
刚好题目还给了我们签名的格式,我们试验一下
得到的sign值为jI6DSECGAyzSs5t5wljIxgp8aBN4SmgzagxSvsv/y3w=,这是经过base64encode的,我们将其解码: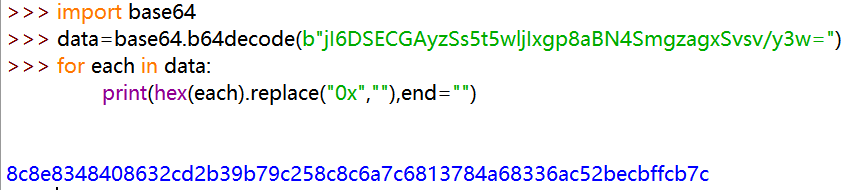
然后明文加密后(记得引号):
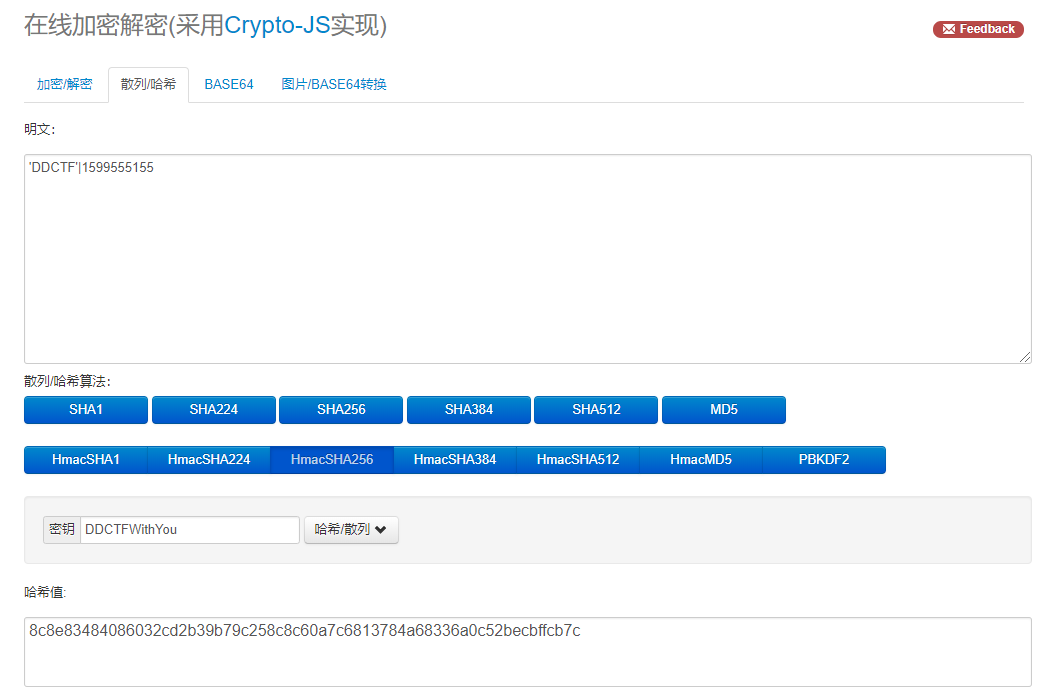
一样的,至此我们的工作结束,贴原WP的脚本:
1 | |
至此,第二关完成。 接下来是最后一关。
最后一关是需要寻找可用payload,是spel注入,也算是SSTI的一种。
参考:
https://www.cnblogs.com/poing/p/12837175.html
https://www.mi1k7ea.com/2020/01/10/SpEL表达式注入漏洞总结/
原WP师傅的脚本是另外起了一个端口用来测试命令,我那个找不到的脚本command是直接嵌到代码里了。这个好像更方便一些
贴原WP的Payload,当时好像测过这个payload但好像失败了。。不知道咋回事,然后就卡在这一步了
new java.util.Scanner(new java.io.File(‘/home/dc2-user/flag/flag.txt’)).next()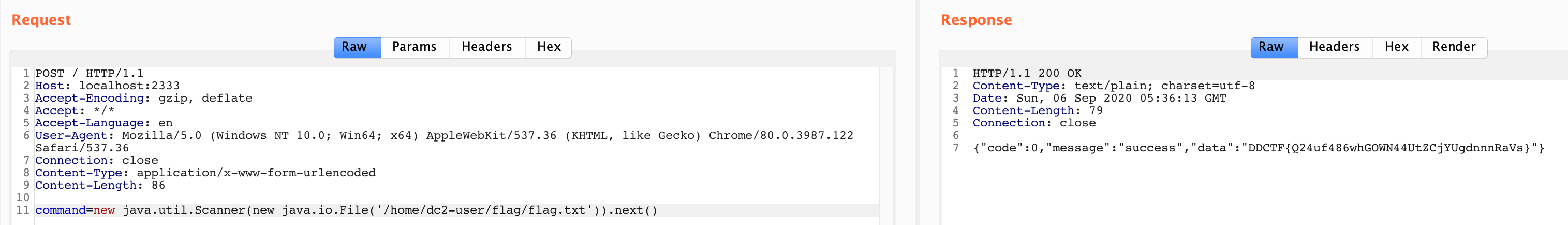
于是可以直接读flag(xmsl)
卡片商店
这题比赛结束后5分钟做出来了。。好气啊
这题一开始以为是条件竞争漏洞,然后写了脚本测了半天,无果。
然后测试发现有整数溢出漏洞(这个也算是购物相关的网站中比较常出现的一个漏洞了,可惜当时一根筋测条件竞争去了,要不还能快点给后面留时间)
执行结果:
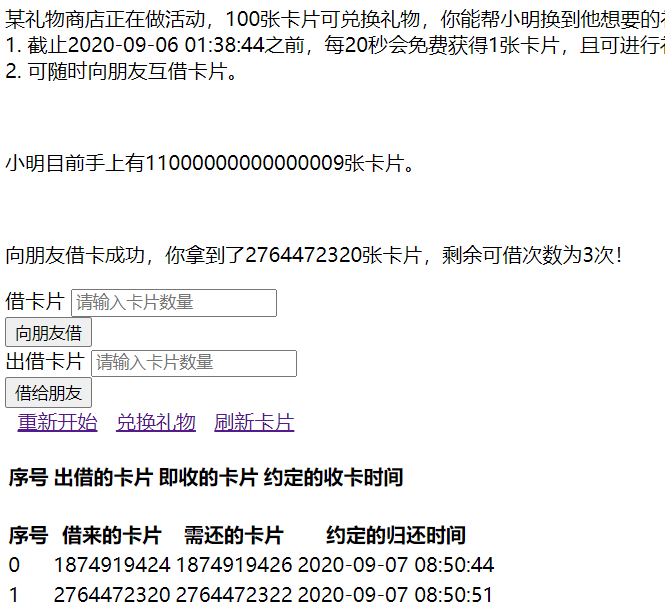
再换掉账面上借的卡片后可以买礼物(这里注意整个过程手速要快,有时间限制)
这个seckey一般就是secretkey,好不好这题刚好有个session:
于是我们可以考虑这个seckey就是用来生成session的。
回过头来,直接访问flag,我们会得到信息
合理推测我们需要伪造session来通过验证拿flag
之前由于出现过Go了,我们考虑gin-session(没get到杜松子酒是gin,跑偏整到Flask那边去了)
参考:https://www.tizi365.com/archives/288.html
现在问题是我们需要伪造哪个字段呢?gin的session我做题时没找到太好的还原方法(原WP最后师傅贴了还原的方法),只能base64解密看看了。一番尝试后得到: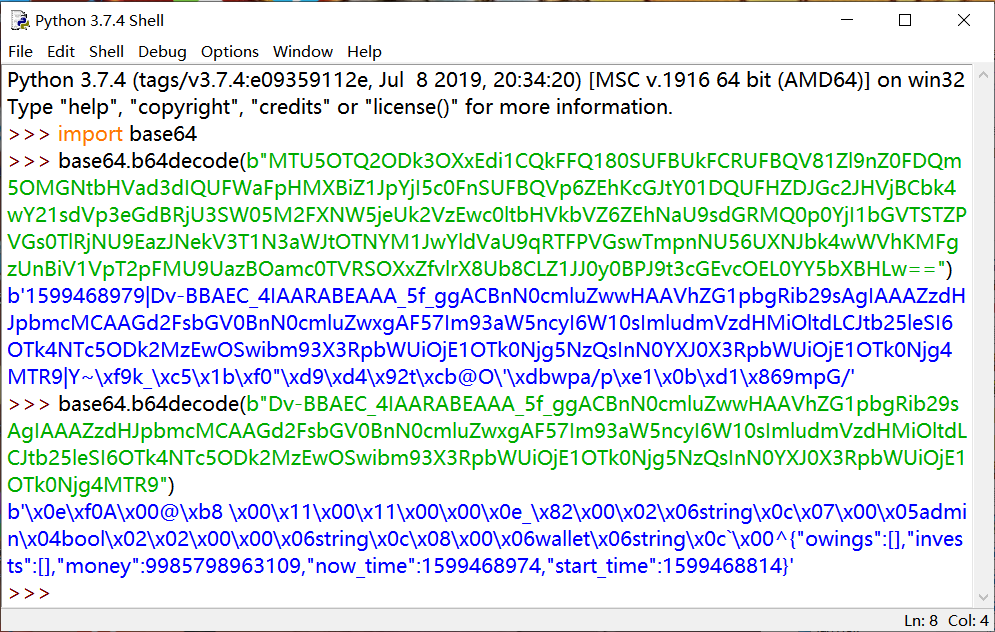
这个方法肯定是有问题的,但也能看出一些信息。这个session的方式应该是 timestamp|Go的encode数据|校验(也可能是签名啥的) 这样的方式,我们也可以看到一个bool类型的admin字段,我们的目标就是它。
贴过来代码:
1 | |
稍作改动即可
1 | |
这里是测试过后发现这样就行的,原本还在后面那块和timestamp那纠结了好久。。后来发现并不需要
拿到session
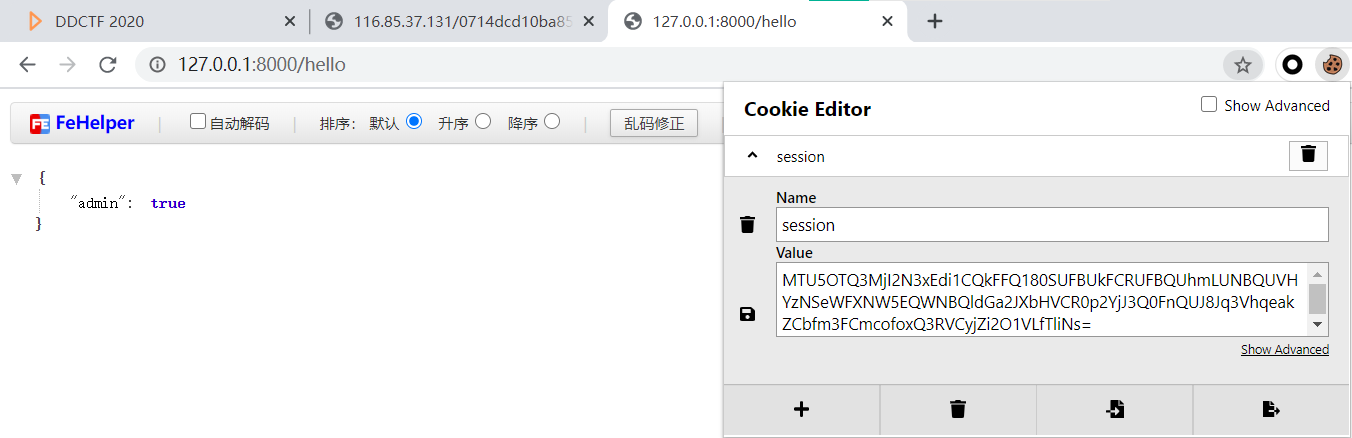
替换后拿flag
Easy Web
考的这个:CVE-2020-11989
这个CVE前几天还看过,差点没反应过来。。
参考:https://xz.aliyun.com/t/7964
但访问
http://116.85.37.131/6f0887622b5e34b5c9243f3ff42eb605/web/index.php
就行(但后面还是要用这个CVE绕进admin界面)
进入界面,这个莫名其妙的图片实在是太显眼了,本能地察觉有问题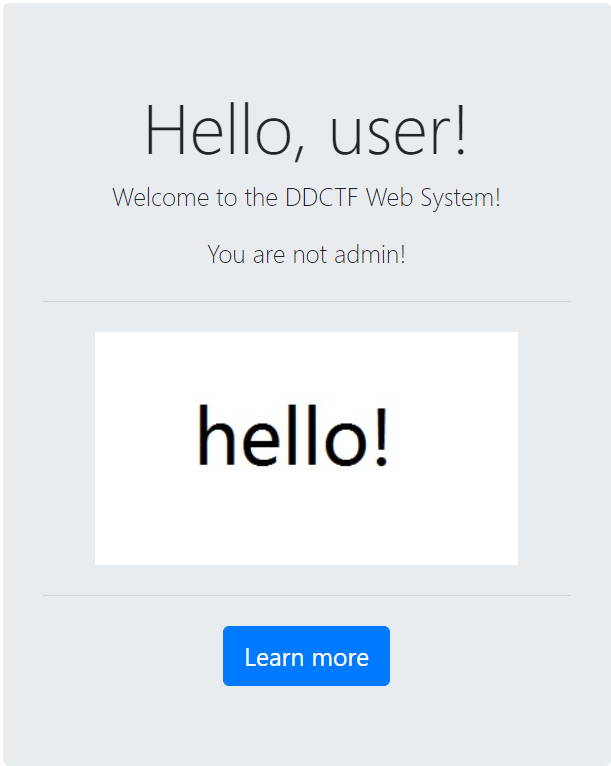
SSRF,然后用fuzzDict中的字典跑了一下,可以读到WEB-INF/web.xml:
http://116.85.37.131/6f0887622b5e34b5c9243f3ff42eb605/web/img?img=WEB-INF/web.xml
1 | |
经典的Spring框架,知道这个对其实我们其实可以直接把大部分代码读出来了。
Spring是一个MVC框架,故读出来的文件中我们需要重点关注的是Controller控制层的代码
根据目前的情况,我们需要寻找能够帮助我们成为admin的信息
一番翻找后,在 /WEB-INF/classes/spring-shiro.xml 中有:
1 | |
其下的 /WEB-INF/classes/com/ctf/auth/FilterChainDefinitionMapBuilder.class 中可以看到
1 | |
于是使用CVE绕过
1 | |
进入admin界面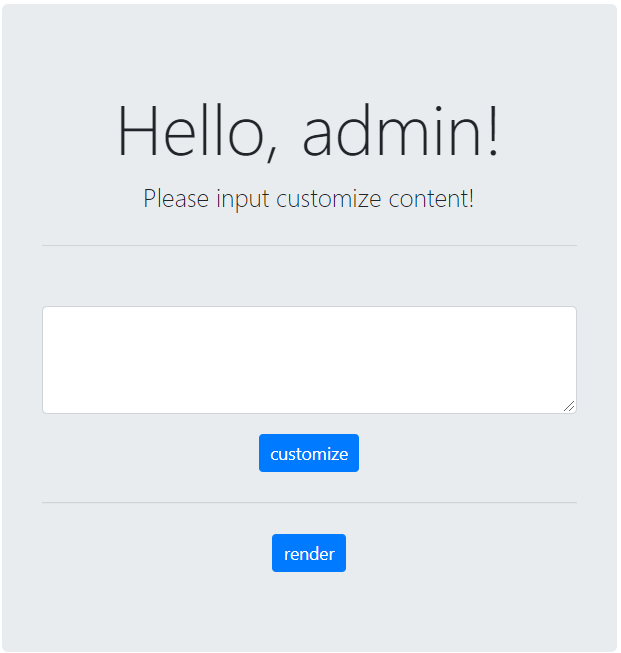
后面就是绕WAF做SpE注入L,WAF在 WEB-INF/classes/com/ctf/util/SafeFilter.class 中
1 | |
后面没绕出来,贴一下原WP的exp:
1 | |
看了看还有另外的思路是使用UrlClassLoader的
见 https://blog.play2win.top/2020/09/07/DDCTF2020_WEB_writeup%20/
Overwrite Me
直接给了源码
1 | |
转了一圈没啥思路,只能试着读那个hint.php
1 | |
然后bullet传进去后显示有个 /FlagNeverFall/suffix_flag.php,然而最后利用的是一个include函数,就算include了没有highlight_file(_FILE_)等我们依然没有办法拿到内容。
后面虽然注意到了$kw0ng这个值有些奇怪,以及看起来似乎有用但不知道有啥用的phpinfo ,但依然没有搜索到有价值的信息,无奈看WP
然后发现 http://117.51.137.166/hint/hint.php 能直接访问。。。一时语塞 个人感觉是题目出糊了,应该是反序列化读 hint/hint.php 来读 flag 的前半部分的(也有可能是干扰项,如果真是这样只能怪自己脑洞太小:) )
写到这里时环境关了。。信息只能从WP拿了
hint.php:
Good Job! You’ve got the preffix of the flag: DDCTF{VgQN6HXC2moDAq39And i’ll give a hint, I have already installed the PHP GMP extension, It has a kind of magic in php unserialize, Can you utilize it to get the remaining flag? Go ahead!
GMP利用相关的参考:
https://xz.aliyun.com/t/6781
https://bugs.php.net/bug.php?id=70513
https://paper.seebug.org/1267/
https://hackerone.com/reports/198734
大致的利用思路就是如果我们有一个可控的反序列化入口,目标后端PHP安装了GMP插件,如果我们找到一个可控的__wakeup魔术方法,我们就可以修改反序列化前声明的对象属性,并配合场景产生实际的安全问题。
一个可行的exp如下:
1 | |
这里WP的师傅说不用 GMP 也能打,这里没太看懂啥意思,Mark一下
1 | |
总结:
这次比赛考的点还是比较新颖的。比如Web和Re结合的Web签到题。。
还有就是不太常见的Go语言这回被拿来出题了,看来还是啥都要会一点
好多题都卡在最后一步可能还是思路还不够广的原因吧,之后还是要多刷点题